Wallet backup
The inheritance wallet described in this reference design is a multi-key wallet with time-based recovery. When backing up such a wallet, users must back up not only their own private keys but also the wallet configuration, as covered here.
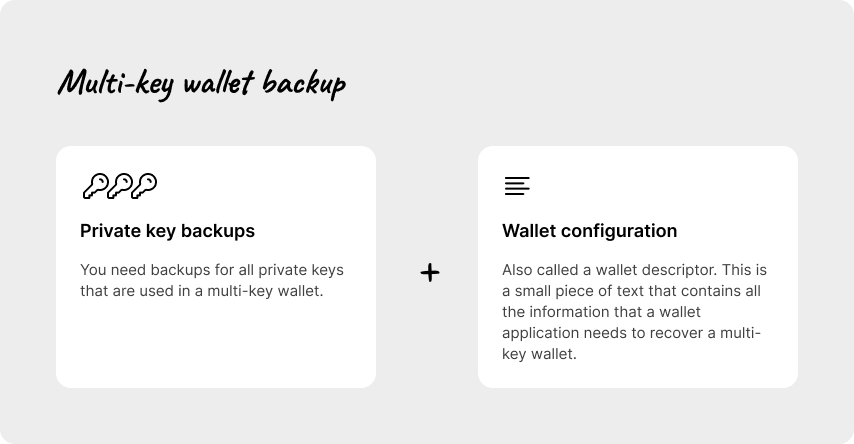
The wallet configuration, also called wallet descriptor, gives a wallet application all the information it needs to generate addresses and identify the rules that define how bitcoin can be spent from these addresses. The private keys are required to sign transactions and spend the bitcoin.
Thus, the Joneses need to safely backup and store six private keys as well as the wallet configuration.
Private key backups #
We have described best practices on how to back up private keys on the bitcoin backups page.
Our app emphasizes that users should keep one of the primary keys at all times, even if they move their funds to a new wallet. The reason is simple: there is still the possibility that some bitcoins will be sent to that old wallet. Keeping one of the keys around will make sure that users will be able to spend such funds, because the recovery path will be available to them.
Wallet configuration backup #
The wallet configuration is backed up in the form of a collection of files packaged into a single backup kit.
Bob saves the backup kit #
Once the wallet is created, the application prompts Bob to download the wallet backup kit. Bob saves the backup kit into his password manager that he has enabled on his phone.
The app shows a reminder to save the backup kit.
The backup page highlights the most important points about the wallet backup and provides a link to learn more.

The file is saved using the native file download flow.
The success screen reminds the user once again to not store the backup kit in the same place as the private key backups.
The app home screen does not show the backup reminder anymore.
Alice and Bob then encrypt the ZIP file with a strong password and both of them stores a copy of it in their personal password manager account, case they need to recover the wallet themselves.
What is in the backup kit? #
The backup kit is a ZIP folder that contains everything Bob and Alice might need to recover their wallet. Either because they replace their mobile phones or because they need to recover the wallet in a different wallet application:
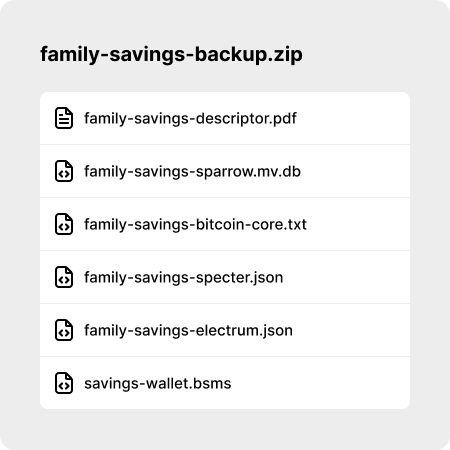
A PDF file that contains a QR code, the wallet descriptor and information about all six signing keys, including their XPUBs. Is also contains a visual representation of the rules that are used to unlock the recovery path and the inheritance key set. You can find an example of the recovery PDF at the bottom of this page.
Wallet backup files in various formats which can be used to import the wallet directly into other wallet applications like Bitcoin Core, Sparrow, Specter, Nunchuk or others.
Backup distribution #
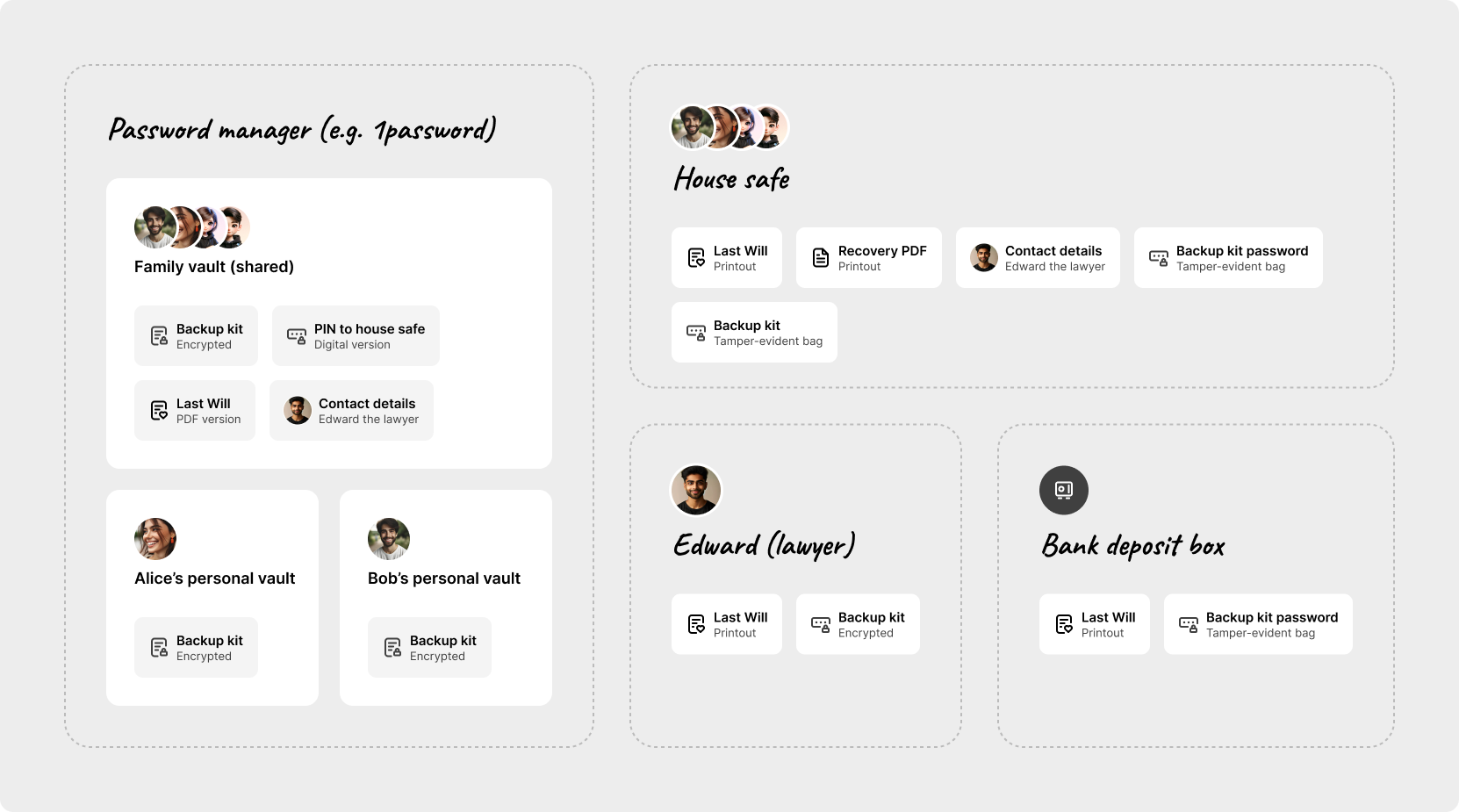
Alice and Bob are not willing to trust their life savings to one application. That’s why they carefully chose the way in which they store the above wallet backup material. The illustration below shows the chosen setup in more detail.
Expand image
Please note that this is one of many possible ways to approach wallet backups and should not be understood as the only correct way to do it.
It is important that users determine the best way to handle backups based on their own specific circumstances. Factors that will influence such decisions include the relationship between family members, the amount of funds stored, their access to safe locations, etc. Based on these and other factors it can be more appropriate to chose a simpler or more advanced backup scheme.
We would also like to reiterate the point made in the “Use case & scope” page: the complexity of the backup scheme increases with the complexity of the wallet configuration. Therefore, user education is critical during wallet creation as well as during the backup phase.
Accessing the backup material #
Christina and David can access the multi-key wallet in two different ways.
Self-sovereign route #
Bob and Alice want to provide the children a way to access the funds on their own, using only the backup parts that are stored in the house safe. They store the password in a tamper-evident bag, along with a USB drive. Since electronics can fail, they also place a printout of their will and the recovery PDF in it.
The PIN to the house safe is stored in the shared family vault in the password manager, where the family also keeps other digital items.
This is an acceptable trade-off for them, since they have good relationships and trust their children. After all, this is the reason they have chosen to include them in the setup in the first place.
Even if Christina and David breach that trust and recover the wallet, they would not be able to move the funds, because their inheritance keys are timelocked. They would only be able to see the balance and monitor transactions, but not spend any bitcoin.
Because Alice and Bob access their safe regularly, they would notice that the bag with the backup material has been opened. They can then safely move the funds to a new wallet, for which they would implement more restrictive security measures.
Assisted route #
But what if the first route fails? In that case, Christina and David should have a way to gain access to the backup material by going through the standard legal procedures. This is why Bob and Alice give their lawyer Edward a copy of the encrypted backup kit. The password is stored in a deposit box at their bank, inside a tamper-evident bag.
This setup will prevent Edward from recovering the wallet, because he does not know how or where to access the backup kit password. It also prevents bank employees from doing so, because the backup kit is not stored in the deposit box along with the password.
But it will enable Christina and David to access both parts of the wallet backup through legal channels upon their parents’ death.
Why backup redundancy? #
The reason that there are two different ways in which Christina and David can gain access to the full backup material is redundancy. Redundancy is important because it is possible that one of the two routes fail.
Example resources #
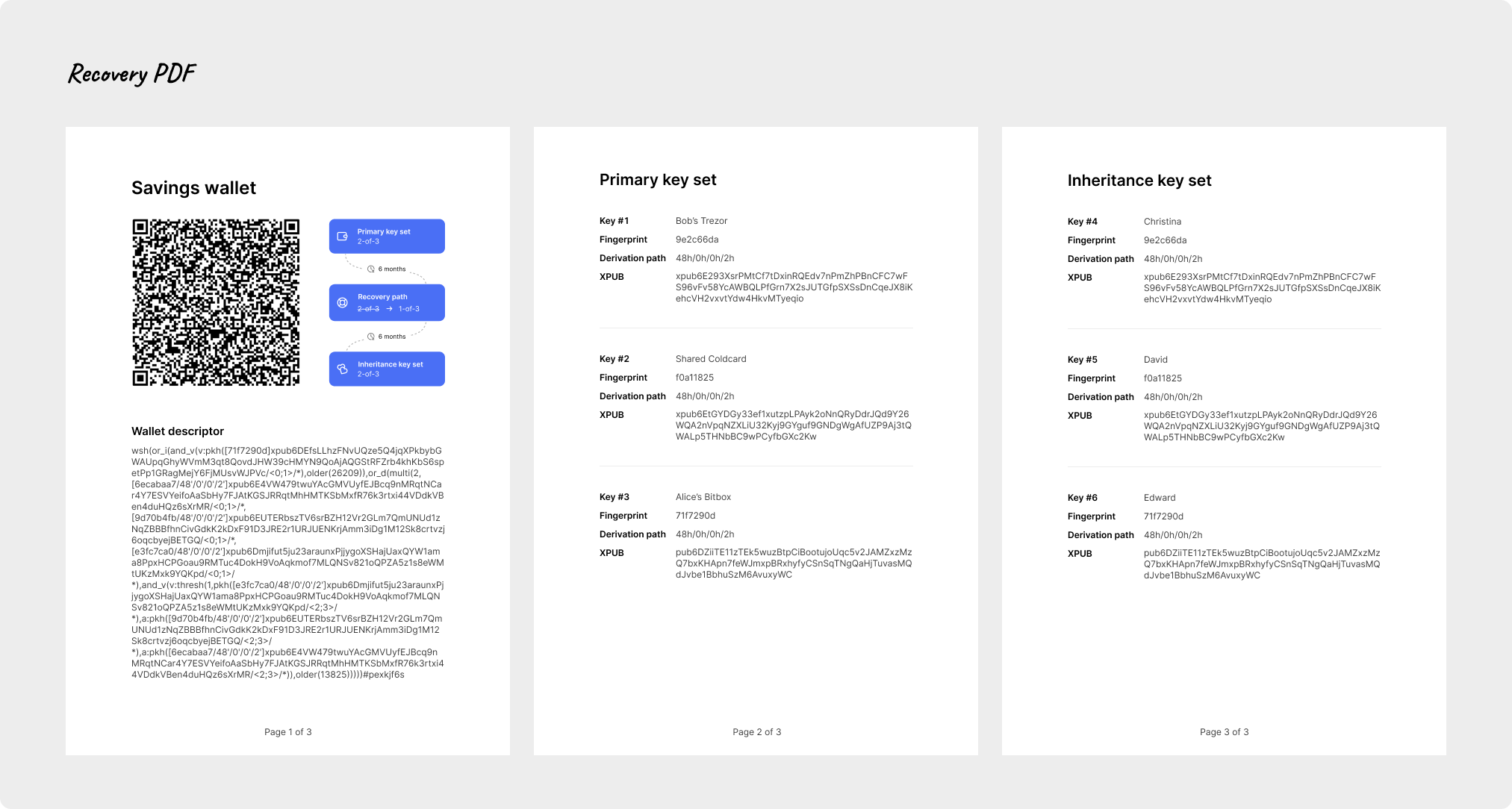
Below is an example of the backup PDF file. The first page contains the information about the wallet itself. This includes the name of the wallet as well as the wallet descriptor in the form of a QR code as well as in clear text. It also shows a visual representation of the configuration of the key sets:
Expand image
The subsequent pages describe the key sets and the individual signing keys, including the friendly names that Bob has given them. This will make it more convenient in case the wallet needs to be recovered.